4 Way Handshake with Wireshark
What happens when you enter wrong password while connecting to Wi-Fi network?
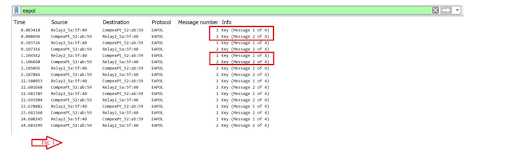
Only 2-way handshake is observed (Fig 1). But why? Let us get in a detail of what happened exactly in this case of WPA2 -PSK authentication.
1st Message:
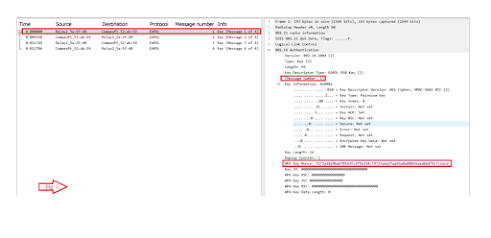
AP sends ANONCE (AP generated random number) along with the MAC address details. Client will generate SNONCE (station generated random number). Now client has PMK, SNONCE,MAC address of the AP and its own MAC address. All these are required to create the PTK for the client (Pairwise Transient Key). (Fig 2)
What is PTK? How it is calculated?
PTK (Pairwise Transient Key) is used to encrypt all unicast traffic between a client and the AP. It is unique between client and AP. Here I addressed some of the important keys that PTK has. They are,
1. KEK (Key Encryption Key) which is used to encrypt the keys. GTK will be encrypted in Message3 using KEK.
2. KCK (Key Confirmation Key) which is used during the creation of the MIC, Hash will be generated using KCK.
3. TK (Temporal Key) which is used for encryption and decryption of unicast packets.
PTK key generation:
PTK = PRF [PMK + ANONCE + SNONCE + MAC(AA) + MAC(SA)] PRF (Pseudo Random Function) is applied to all the inputs.
ANONCE is a random number generated by AP.
SNONCE is a random number generated by client.
MAC(AA) mac address of the AP (authenticator).
MAC(SA) mac address of the client (supplicant).
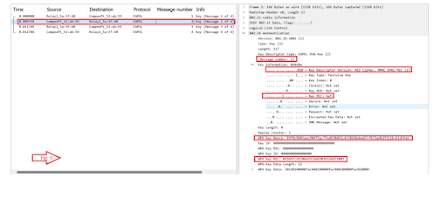
2nd Message:
The client sends to the AP its SNONCE and encrypted part of PTK (i.e.) MIC (Message Integrity Check).
Why is MIC introduced? How is MIC calculated??
The keys generated should never be sent over the air. So, the concept of MIC verification has come up.
WPA2 PSK- uses HMAC-SHA1 (Hash-Based Message Authentication Codes) to generate the MIC and it uses the KCK (Key Confirmation Key) to generate hash.
Now Access point can then use the MIC to verify that the message has not been tampered during transmission. Now AP got all the parameters required for computing PTK.
Once the AP receives that packet (here with wrong credentials) It will check by verifying MIC (Message Integrity Check). AP compares the MIC sent by the client with the MIC that AP has generated with details received in the 2nd message. If the MIC is not same, it is because PMK from client side is different from the PMK on AP side (i.e., Password given by the client is wrong)
Thus, as a result only 2-way handshake happens due to failure in MIC validation.
Here is the process when we enter the right password.
In 3rd message, AP derives the GTK.
How does GTK works?
GTK (Group Temporal Key) is helpful to encrypt the broadcast and multicast traffic between the clients and the AP. Now AP will send the GTK to the client and the GTK will be encrypted using KEK (Key Encryption Key).
KEK (Key Encryption Key) which is used to encrypt the keys. GTK will be encrypted in 3rd Message using KEK to deliver to the client.
Then AP asks the client to install the temporal keys.
4th Message: It is confirmation message from client to the AP that the temporal keys has been installed successfully.
So, after the 4-way handshake, the data frames (MSDU) will be encrypted using PTK or GTK keys depending upon unicast or multicast/broadcast frame.








Comments
Post a Comment